Bitcoin mining refers to the security mechanism implemented into the Bitcoin protocol to achieve consensus over the state of the blockchain, in a decentralized way. It is key to understand how that mechanism prevents someone from cheating the system, thereby making the network not only more secure, but antifragile too.
It can be hard to wrap your head around Bitcoin, both on a conceptual and on a technological level. It is unique in many ways and its use cases might not seem clear at first. For that reason, the Bitcoin community and the media came up with many analogies to make it easier for less tech savvy people to visualize what Bitcoin is. One such analogy you might have heard of is the famous digital gold narrative. This analogy appeared relatively early in Bitcoin’s history, partly to justify its existence and partly to relate it to something people knew and understood. As such, the most early adopters started using the term bitcoin mining to draw a parallel with gold mining.
Fun fact: the term ‘mining’ is never used in the Bitcoin White Paper, neither is the term ‘blockchain’.
Still, the term is quite vague and does not really explain how the ‘mining’ takes place.
The goal of this article will be to help you understand how bitcoin mining actually works. We will explain what terms like Proof Of Work (or POW), cryptographic puzzle and hash functions mean and how they all come together under the popular term ‘bitcoin mining’. The difference between a transaction validation and a transaction confirmation will also be explained. Technical words will be highlighted in bold and explained throughout the article and you will also find below an infographic of the whole process.
What is bitcoin mining?
Bitcoin mining essentially consists of solving (or attempting to solve) a simple cryptographic puzzle, which when solved, proves mathematically that a set of bitcoin transactions are valid. You can think of this cryptographic puzzle as trying to find the code of a lock. There are no shortcuts possible when trying to find the code which unlocks it. You have to try every possible combination, until at some point, you find the correct one by chance. I like this analogy because it describes well the characteristics of the cryptographic puzzle used by Bitcoin. Just like trying to find the combination that unlocks the lock, trying to find the correct solution to the puzzle is very time and energy consuming. Just as it is extremely easy and quick to check that the combination is the correct one (it either unlocks or doesn’t), it is extremely easy and quick for the miner, and for other miners after, to check that the solution proposed to the puzzle is indeed the right one.
This process of attempting several solutions until encountering the correct one is called Proof of Work (or POW) and the cryptographic puzzle (or POW algorithm) in the Bitcoin protocol uses SHA256 , which stands for “Secure Hash Algorithm”. Since miners expand so much time and energy to solve this puzzle and thus validate transactions on the Bitcoin blockchain, the protocol rewards them for their effort with:

- The newly created bitcoin
When a miner validates the transactions, they are bundled in a block and added to the Bitcoin blockchain. And for every new block that gets added to the blockchain, new bitcoins are created according to the issuance rate determined by the protocol at the time of the block creation. At the time of writing, new issuance is 12.5 BTC per block and is expected to halve around May 2020.
2. The total of all transaction fees for the transactions they validated
When people transact with bitcoin, they pay a fee to the miners to incentivise him further to validate their transaction. Thus, when a miner validates a set of transactions, he also collects all the fees paid for that set of transactions. As of now, this represents a very small percentage of the total mining reward, but as the issuance rate decreases, the fees will become a more significant source of income for miners.
But how can solving a puzzle prove that a transaction is valid?
In order to answer this, we need to refer back to the PoW algorithm we mentioned earlier (SHA256) and we need to explain what a hash is.
Simply put, a hash is a string of characters. This string of characters is the output of a special function called a hashing function. Hash functions are special because they can take any (literally any) series of digital data (a text file, a video, a picture, a song anything) as input and transform it into a single string of characters. What makes this function even more special (and more interesting in our use case), is that if you change even one character in the input (or one byte really), the output string, or hash, will be completely different with no link whatsoever to the previous output.

At this point it might still seem unclear how SHA256 works and how it helps miners reach consensus on the state of the blockchain. To understand this, it is important to recall what information is included in Bitcoin blocks, or most importantly, how transactions are included in Bitcoin blocks. Most information contained in a Bitcoin block on the blockchain is represented by a hash and every block itself is tied to a unique hash. Let’s list some of the essential elements which are combined to generate a Bitcoin block hash:
- Transactions’ hash
The hash of the list of all transaction hashes included in the block. A transaction hash is created by combining the following elements into a single hash: the sender’s hash, the receiver’s hash and the amount sent (ie: the UTXO’s, read more about them here).
2. Previous block’s hash
Computed in a similar way. Only the very first block (called genesis block) does not use the previous block’s hash.
3. Nonce
The nonce is the key to the puzzle. It is a positive integer number, which when combined with the previous two elements (transactions hash + previous block’s hash), creates the final block’s hash.
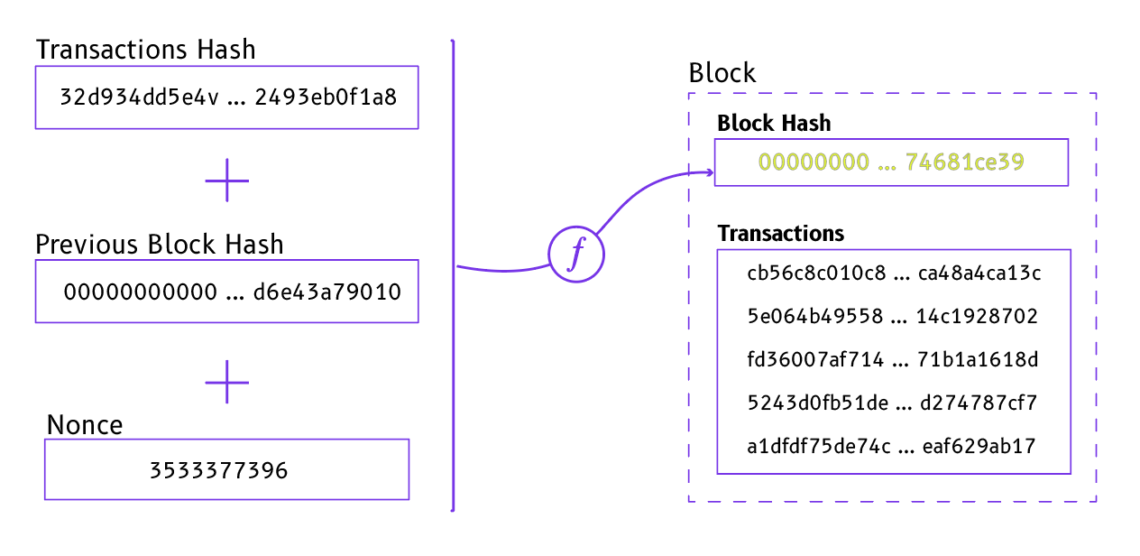
In SHA256, the condition which needs to be met to ensure the correct nonce was found, is that the block’s hash should start with a series of zeros. That is, when we input into the hashing function: the transactions’ hash, the previous block’s hash and the nonce, the output hash should start with a series of zeros. The way the hashing function works ensures that there is only one possible solution (ie: only one nonce which leads to such a hash). In the same way there is only one combination that unlocks the lock in our previous analogy.
So the nonce is the key to the cryptographic puzzle, but what really makes this a beautiful and secure algorithm is the fact that it requires the hash of the previous block as an input to find the solution. It is one of the three key elements composing the final block hash. Recall that the property of a hashing function is that any change in the input completely changes the output with no deterministic link to the previous output. Therefore, even a slight change in any of the inputs (say a change of amount sent in one of the transactions) changes the final hash and invalidates the nonce.
Why does that algorithm make the transaction secure and prevent changes?
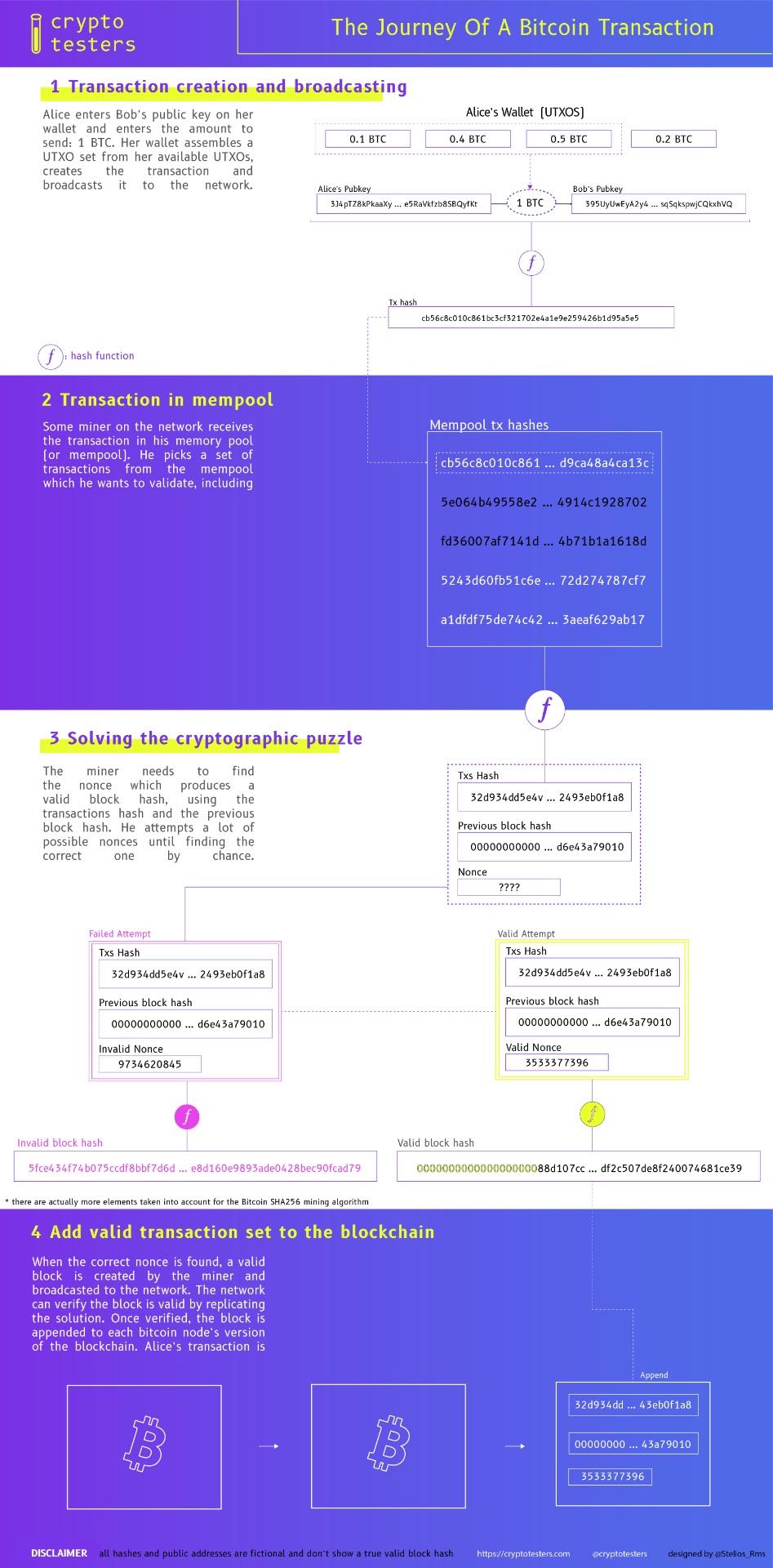
To understand how the algorithm introduces security and truly validates the transaction set in the block, let’s go over a simple example. Imagine the situation where Alice sends Bob 1 BTC. After signing this transaction with her private key, Alice’s bitcoin wallet will broadcast it to the network and will enter the miners’ unconfirmed transactions pool. After some time, a miner will pick it up alongside a set of other transactions and attempt to find the correct nonce and create the next block. The transaction is hashed into what we will refer to as the transactionHash. Then that hash is used in combination with all other transaction hashes in what we will refer to as the transactionsHash. Finally, the miner combines the transactionsHash with the previous block hash and looks for the correct nonce that would output a final block hash starting with a series of 0s, which we will refer to as the blockHash. After a while, the miner finds the solution, shares it with the rest of the network and appends the block to the blockchain. So far so good.
Now imagine that Alice wants to trick Bob and instead of sending him 1 BTC she tries to change the record to 0.5 BTC. By doing that, she inevitably changes the transactionHash, which in turn changes the transactionsHash, which consequently changes the blockHash. Now, the blockHash no longer starts with a series of 0s and the nonce is no longer valid. Therefore if Alice wanted to force that change, she would have to mine the block again and broadcast her solution. However, in the meantime, other miners are already looking for the next block which uses the previous’ block hash as a piece of the puzzle. Here it’s important to note that, by convention, the miners always use the longest chain (blockchain with most validated blocks) as the valid chain. So if Alice wants to change the block she would have to mine her block and the next one, faster than all the other miners, in order to produce the longest chain. However, since she has attempted to modify an existing block, she is already behind! She would have to spend a lot more energy to first catch up with the other miners and then produce the next blocks faster.
As it stands, such an attack would be extremely costly and would not be worth any change done to the transaction. This becomes even more true as the block moves deeper in the history of blocks. Indeed, if Alice wanted to change a transaction that happened 10 blocks in the past, she would have to mine all 10 blocks as they all depend, up to the latest one, on the hash of the previous block. It becomes even more costly considering the fact that a successful attack would likely be quickly identified and destroy the value of the very asset they were trying to earn more of. And that is how a combination of cryptography and well-aligned incentives produce a truly secure algorithm.

What if someone wanted to attack the network just to destroy it?
We’ve shown the economic incentive of an attack makes little sense, but what if someone wanted to attack Bitcoin just to destroy it? Is that possible? The attack described above is also known as a 51% attack, where the attacker assembles 51% of the total processing power of all miners. By owning more than half the processing power, the attacker would statistically find blocks faster and thus be able to change a block and produce the longer chain. At the time of writing, the total processing power of all mining operations, or hashrate, is 108,616,441 TH/s. Which means that all miners combined, try more than one hundred million trillion nonces every second. Getting 51% of that hashrate is unimaginable, even for a nation. It would take enormous resources and mobilisation to successfully conduct such an attack. And with every increase in hash rate,this becomes less and less likely.
With such a high hashrate, shouldn’t the correct nonce be found extremely quickly?
This is a question that oftens comes back. We know that block times for Bitcoin is about 10 minutes. So how does it stay at 10 minutes and what stops miners that try millions and millions of nonces to not find it within a few seconds? The Bitcoin protocol includes a mechanism called difficulty adjustment that prevents this from happening. Difficulty adjustment increases the pool of possible nonces to make it less likely to find the correct one. You can think of it as increasing the number of digits in the combination that unlocks the lock. If 1 000 people are looking for a five-digit combination, they are likely to find it very quickly. But if they are looking for a 100-digit combination, it will take them significantly longer. So based on the current hashrate, the difficulty adjustments computes the necessary difficulty to keep the block times around 10 minutes and maintain the bitcoin issuance rate as specified by the protocol.
What’s the difference between a transaction validation and a transaction confirmation?
You might have seen on exchanges that a transaction needs a minimum number of confirmations before your deposit can be credited. A transaction confirmation happens every time the block in which your transaction was first confirmed moves deeper in the blockchain. So, a transaction validation is when the transaction is first added to a block and transaction confirmations happen whenever a new block (based on that one) is mined. As we mentioned above, a block that is deeper in the chain is harder to revert.Therefore, a higher number of confirmations makes it more secure.
Is ‘bitcoin mining’ really a good analogy?
Analogies are great for simplifying abstract concepts or complex ideas but they often fall short of explaining the underlying processes. Therefore, as great as the term bitcoin mining is to understand its purpose (i.e.: create new bitcoins and increase circulating supply just as gold mining does), it tells you absolutely nothing about the process. In fact, it can conversely create a lot of confusion around what bitcoin mining is and undermine the importance of mining as a key factor of Bitcoin’s security, decentralisation and scalability. Indeed, with the total supply of bitcoins being capped at 21 million, bitcoin mining won’t create new coins forever, yet the so-called “mining” will still have to continue to validate new transactions. People can only speculate what would happen after all coins have been issued. The most likely outcome is that a fee market will develop and self-regulate to keep miners incentivised. However, we are still decades away from seeing that happening and, chances are, if Bitcoin is still around then, it will have grown into a much, much larger asset than it is today. Let us conclude this article with a small speculative projection of what such a future might be like:
Bitcoin will become the international monetary standard and validating the network will be a matter of national security and sovereignty. Fees on the first layer will be much higher (not necessarily nominaly, but in purchasing power) and transactions will consist of massive international settlements between 2nd layer liquidity providers (imagine bank settlements today) while small transactions will take place on 2nd and 3rd layer solutions with much lower fees.
About the Author:
I’m a data scientist with a passion for bitcoin. My goal is to help people navigate this field by writing detailed and comprehensive articles. To stay updated on my latest pieces and contributions for Cryptotesters, follow me on Twitter at @Stelios_Rms